
Automated anomaly detection is transforming how security camera systems protect properties and people. When your platform can automatically spot unusual activities, it creates a smarter, more reliable security solution for your clients. Think of it like having thousands of alert, tireless observers who never miss a detail - that's what good automation brings to your security cameras.
Our experience with the V.A.L.T. project shows how this works in real life. While users see a simple interface for streaming IP cameras and managing recordings, the smart technology running behind the scenes does the heavy lifting. The system watches for anything out of the ordinary, helping security teams focus on real issues instead of monitoring endless footage.
Want to add this kind of smart detection to your platform? We'll show you practical ways to build automated anomaly detection into your security camera system, making it more valuable for your users while keeping the technology straightforward and effective.
Key Takeaways
- Use unsupervised machine learning models to detect unusual patterns without labeling
- Define normal behavior by analyzing historical video data and establishing baselines
- Optimize real-time anomaly detection with edge computing to reduce latency
- Combine unsupervised techniques with convolutional neural networks for enhanced accuracy
- Regularly review and adjust sensitivity settings to minimize false alarms while capturing genuine anomalies
Why Trust Our Video Surveillance AI Expertise?
At Fora Soft, we've been at the forefront of video streaming and AI-powered multimedia solutions since 2005. Our 19+ years of specialized experience in developing video surveillance systems has given us unique insights into implementing effective anomaly detection solutions. We've successfully delivered numerous projects for law enforcement agencies and medical institutions, maintaining a remarkable 100% project success rating on Upwork.
Our team's expertise in AI recognition technology and video streaming is demonstrated through our work with various platforms, including our V.A.L.T system. We've tackled complex challenges such as managing multiple HD video streams while maintaining perfect audio-visual synchronization, implementing advanced encryption protocols, and developing sophisticated permission controls. This practical experience allows us to provide actionable, tested advice on implementing machine learning for anomaly detection in security camera footage.
🔍 Curious about our track record? Take a peek at our impressive portfolio of AI projects or schedule a friendly chat to discuss how we can enhance your surveillance systems. No strings attached – just pure expertise sharing!
Tip # 1: Use Machine Learning

To effectively detect anomalies in security camera footage, you should utilize machine learning techniques. Unsupervised learning models can identify patterns and flag unusual events without explicit labeling, while convolutional neural networks (CNNs) excel at analyzing visual data. Research has shown that unsupervised anomaly detection algorithms are particularly effective at capturing previously unseen anomalies, performing well when identifying novel types of intrusions (Zoppi et al., 2021). By combining these approaches, you can create a strong system that accurately detects anomalies in real-time.
As demonstrated in our V.A.L.T platform, combining these approaches creates a robust system that accurately detects anomalies in real-time, particularly beneficial for police departments and medical institutions requiring precise monitoring.
Employ Unsupervised and CNN Models
Employ unsupervised learning algorithms like k-means clustering and convolutional neural networks (CNNs) to detect anomalies in security camera footage without relying on labeled training data. These anomaly detection algorithms can identify unusual patterns and abnormal event detection in video streams. Deep reinforcement learning techniques have shown remarkable success in video surveillance applications, demonstrating improved detection rates through dynamic environmental learning (Aberkane & Elarbi-Boudihir, 2022). A deep learning model such as a convolutional autoencoder is well-suited for video surveillance anomaly detection tasks, similar to how our V.A.L.T system processes HD video streams for medical education institutions and law enforcement agencies.
The autoencoder learns to reconstruct normal video frames, so anomalies produce higher reconstruction errors. The role of autoencoders in generating quality latent representations has been emphasized, where effective feature extraction can lead to high anomaly detection accuracies (Wang et al., 2023). Clustering algorithms then group these anomalous frames. CNNs excel at analyzing visual data by learning hierarchical features, supporting the premise that reconstruction error is vital in maintaining data integrity.
Combining unsupervised techniques with deep CNN architectures enables strong, automated detection of anomalies in security video footage, flagging events of interest for review. This approach scales well to handle the large volumes of video data generated by surveillance systems.
Combine Models for Accuracy
Combining multiple machine learning models can further improve anomaly detection accuracy in security camera footage. By integrating different approaches like unsupervised learning and convolutional neural networks (CNNs), you can create a more sturdy anomaly detection model. Recent advancements in deep learning models that incorporate both temporal and spatial features have achieved remarkable accuracy rates of 98.94% in detecting anomalies (Yin et al., 2023).
Our experience with V.A.L.T has shown that this combined approach is particularly effective for real-time applications in sensitive environments like police interrogations and medical training sessions. This combined model utilizes the strengths of each individual technique to better identify unusual patterns and behaviors in surveillance videos.
It's especially effective for real-time applications, where quick and accurate detection is vital. The model can be trained on diverse datasets covering various scenarios of human behavior, allowing it to detect a wide range of anomalies.
Combining models not only enhances accuracy but also reduces false positives, ensuring that security personnel can focus on genuine threats.
Tip # 2: Optimize Real-Time Processing
To optimize real-time processing for your anomaly detection system, you should implement edge computing techniques. This approach involves processing data closer to the source, such as on the security cameras themselves or on nearby edge servers, which reduces latency and enables instant alerts when anomalies are detected.
Implement Edge Computing
Edge computing often reduces latency, enabling real-time anomaly detection in security camera feeds. In fact, edge computing can reduce latency to under 50 milliseconds, making it ideal for real-time processing applications (Yuan, 2025). By processing video surveillance data at the edge, you can quickly identify anomalous events without relying on cloud servers. This approach utilizes artificial intelligence and machine learning algorithms to perform detection in videos using edge computing devices.
These devices, such as smart cameras or edge gateways, analyze the video stream locally and trigger alerts when suspicious activities are detected. Edge computing minimizes bandwidth usage and guarantees rapid response times, which are vital for security applications. It also enhances privacy by keeping sensitive data within the local network.
To implement edge computing for anomaly detection, consider using specialized hardware accelerators and optimized software frameworks that can handle the demanding computational requirements of real-time video analysis.
Ensure Instant Alerts
Instant alerts are essential for security camera systems, guaranteeing timely responses to potential threats. Optimizing real-time processing is key to achieving this goal.
Here's how you can guarantee instant alerts for suspicious activities in your video surveillance setup:
- Implement advanced algorithms that can quickly identify abnormal activity in video feeds.
- Utilize edge computing to process data closer to the source, minimizing latency.
- Set up automated notifications via SMS, email, or push notifications for immediate action.
Tip # 3: Define Normal Behavior
To effectively implement anomaly detection on your platform's video surveillance features, you'll need to establish a clear understanding of what constitutes normal behavior in various security camera setups. Start by providing tools that analyze historical data from users' cameras to identify patterns and create baselines for typical activity levels, movement patterns, and object interactions.
Once these baselines are defined, configure your platform's anomaly detection system to monitor live video feeds and flag any notable deviations from the established norms in real-time. This approach allows your platform to offer customized, context-aware anomaly detection for each user's unique security environment.
Establish Baselines from Historical Data
By analyzing historical video footage, you can establish baselines that define what constitutes normal behavior in each camera's field of view. This vital step allows your system to accurately identify abnormal events and anomalies.
To create effective benchmarks for normal behavior, you'll need to process a substantial amount of historical video data, focusing on typical patterns of movement, object interactions, and environmental conditions. Recent research has shown that advanced autoencoder techniques can significantly improve anomaly detection through vector reconstruction error approaches, particularly in complex cloud network environments (Torabi et al., 2023). By training your anomaly detection algorithms on these benchmark datasets, you can markedly improve the accuracy and reliability of your automated video surveillance anomaly detection system in real-world scenarios.
Keep in mind that the more thorough and representative your historical data is, the better your system will be at distinguishing between normal and abnormal events, minimizing false alarms and missed detections.
Detect Deviations in Real-Time
Once you've established baselines for normal behavior, you can configure your anomaly detection system to identify deviations in real-time. By utilizing advanced techniques like neural networks, your video surveillance solution can continuously analyze incoming footage and compare it against the defined norms. This enables the system to swiftly detect abnormal behavior, such as unauthorized access, suspicious movements, or atypical crowd patterns.
However, it's essential to fine-tune the sensitivity settings to strike a balance between capturing genuine anomalies and minimizing false alarms. Context-aware anomaly detection in big data streams can translate anomalies into critical information, improving the understanding of underlying patterns and enhancing detection capabilities (Hussien & Dowaji, 2018). Regularly review and adjust these parameters based on real-world performance to optimize the system's accuracy.
By promptly alerting security personnel to verified deviations, you can guarantee a rapid response to potential threats and maintain a secure environment for your organization.
Interactive Anomaly Detection Configuration Assistant
Finding the right balance for your security camera's anomaly detection system can be challenging. This interactive tool helps you visualize how different sensitivity settings affect detection accuracy across various security scenarios. Adjust the sliders to see how changes impact both false positives and missed detections in real-time, helping you implement the article's key concepts in your own security solutions.
Real-World Implementation: V.A.L.T Platform Experience
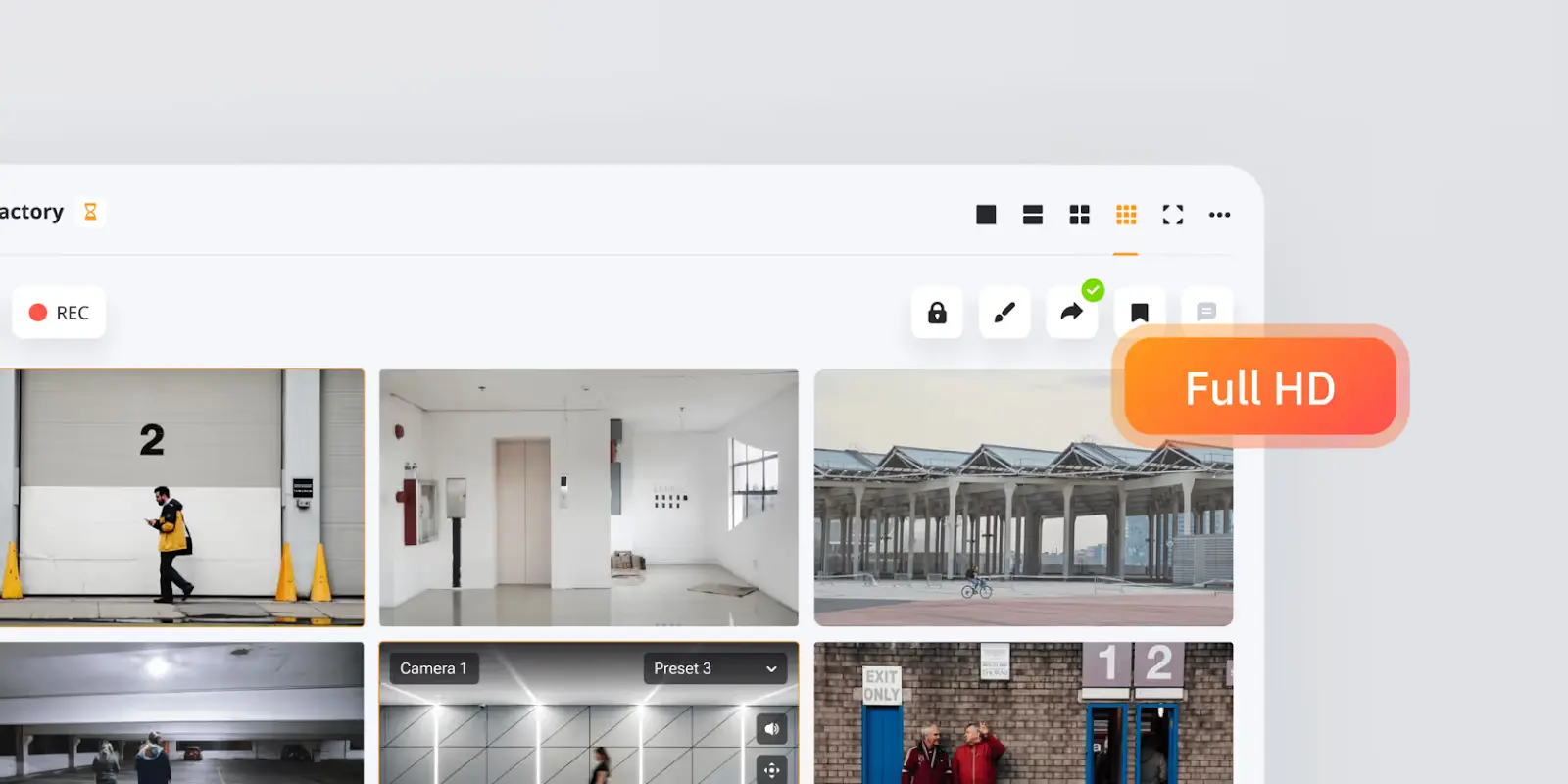
In developing the V.A.L.T video surveillance platform, we faced the challenge of creating a system that could handle multiple HD video streams while maintaining perfect audio-visual synchronization. Our solution incorporated advanced encryption protocols (SSL and RTMPS) and sophisticated permission controls, crucial for organizations dealing with sensitive information. The platform's success in medical education institutions and police departments demonstrates the effectiveness of implementing proper anomaly detection and security measures in real-world scenarios. Through careful architecture design and optimization, we achieved a scalable system that can support an unlimited number of users and cameras without compromising performance or security.
🎯 Inspired by what's possible? Explore our AI integration services or book a consultation to discuss your specific needs. We're here to turn your vision into reality!
Frequently Asked Questions
What Types of Cameras Are Compatible With Automated Anomaly Detection Software?
You can use most IP cameras with automated anomaly detection software. Confirm your camera supports RTSP streaming and has sufficient resolution. Compatible brands include Axis, Hikvision, and Bosch, but check with your software provider for specific requirements.
How Much Training Data Is Required for Accurate Anomaly Detection?
You'll need a substantial amount of training data, typically hundreds or thousands of labeled examples, for accurate anomaly detection. The more diverse and representative your dataset, the better the algorithm will perform in real-world scenarios.
Can the System Adapt to Changing Environments and Behaviors Over Time?
Yes, with continuous learning, your anomaly detection system can adjust to evolving environments and behaviors. It updates its models as new data arrives, ensuring accurate detection even as patterns change over time.
What Is the False Positive Rate for Detecting Anomalies?
To minimize false positives, you'll want to fine-tune your anomaly detection thresholds based on real-world data. Expect some trial and error to find the right balance between catching true anomalies and avoiding excessive alerts.
How Does the System Handle Low-Light or Poor Visibility Conditions?
To handle low-light or poor visibility, you'll want to use cameras with infrared night vision and advanced image processing algorithms. These can clean up noisy images and detect anomalies even in challenging lighting conditions.
To Sum Up
By implementing these three tips, you can markedly enhance your security camera's automated anomaly detection capabilities. Machine learning models will accurately identify unusual patterns, while defining normal behavior will allow for real-time detection of deviations. Optimizing processing through edge computing guarantees instant alerts and swift responses to potential threats. Incorporating these strategies will provide a strong, efficient, and effective anomaly detection system, ultimately bolstering the security of your monitored premises.
🚀 Ready to elevate your video surveillance system? Our team is just one click away! Schedule a call today and let's discuss how we can help you implement these proven strategies. Don't let another day pass with suboptimal security – your peace of mind is worth it!
References
Aberkane, S., & Elarbi-Boudihir, M. (2022). Deep reinforcement learning-based anomaly detection for video surveillance. Informatica, 46(2). https://doi.org/10.31449/inf.v46i2.3603
Hussien, A., & Dowaji, S. (2018). A novel framework for context-aware outlier detection in big data streams. Journal of Digital Information Management, 16(5), 213. https://doi.org/10.6025/jdim/2018/16/5/213-222
Torabi, H., Mirtaheri, S., & Greco, S. (2023). Practical autoencoder based anomaly detection by using vector reconstruction error. Cybersecurity, 6(1). https://doi.org/10.1186/s42400-022-00134-9
Wang, F., Cheng, F., & Zhang, M., et al. (2023). Self-supervised learning for textured surface anomaly detection and localization. https://doi.org/10.1117/12.2673155
Yin, J., Zhang, C., & Xie, W., et al. (2023). Anomaly traffic detection based on feature fluctuation for secure industrial internet of things. Peer-to-Peer Networking and Applications, 16(4), 1680-1695. https://doi.org/10.1007/s12083-023-01482-0
Yuan, H. (2025). Optimization techniques for real-time optical image processing using edge computing. https://doi.org/10.1117/12.3059702
Zoppi, T., Ceccarelli, A., & Bondavalli, A. (2021). Unsupervised algorithms to detect zero-day attacks: Strategy and application. IEEE Access, 9, 90603-90615. https://doi.org/10.1109/access.2021.3090957













.avif)

Comments